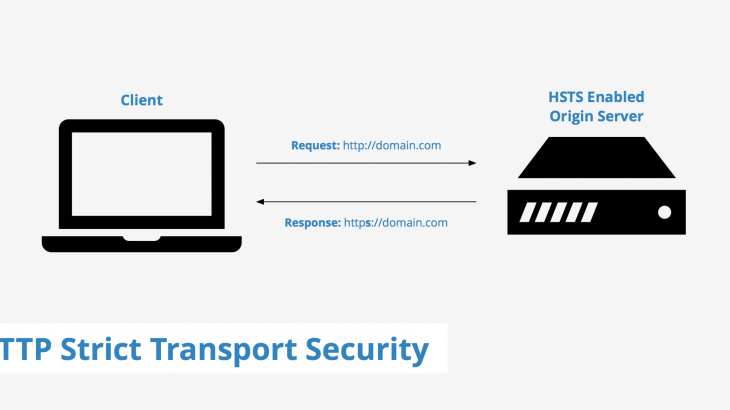
HTTP Strict Transport Security Policy (HSTS) protects your website from malicious attacks like man-in-the-middle attack, protocol downgrade attack and cookie hijacking. It allows servers to specify that they use only HTTPS protocol for requests and web browsers should send only HTTPS requests. However, HSTS is disabled by default in Apache server. In this article, we will look at how to enable HTTP Strict Transport Policy in Apache server.
How to Enable HTTP Strict Transport Policy in Apache
Here are the steps to enable HSTS in Apache server.
1. Enable mod_headers
We will be setting a request header in Apache server using mod_headers module. Depending on your Linux system, run the following commands to enable mod_headers
Ubuntu/Debian
Open terminal and run the following command to enable mod_headers
$ sudo a2enmod headers
Redhat/CentOS/Fedora
Open terminal and run the following command to open Apache configuration file. It is located at any of the following locations depending on your installation.
- /etc/apache2/httpd.conf
- /etc/apache2/apache2.conf
- /etc/httpd/httpd.conf
- /etc/httpd/conf/httpd.conf
$ sudo vi /etc/apache2/httpd.conf
Uncomment the following line by removing # at its beginning.
#LoadModule headers_module modules/mod_headers.so
Also read : How does RewriteBase work
2. Enable HTTP Strict Transport Security (HSTS)
Open the virtual host configuration file for your website located at /etc/apache2/sites-available. If you have not created a virtual host configuration for your website, then open the default one.
$ sudo vi /etc/apache2/sites-available/000-default.conf
Look for <VirtualHost *:443> block that listens to port 443.
Add the following line in the tag.
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
Let us look at the above line in detail.
- max-age – the amount of time browsers must enforce HSTS headers. We have specified it as 1 year
- includeSubDomains – Apply HSTS for subdomains also
So your VirtualHost tag will look like
<VirtualHost *:443> ... Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains" ... </VirtualHost>
Please note, you need to add the Header directive to virtual host listening to port 443 (SSL/HTTPS) only.
Also read : How to Change Log Level in Apache Server
3. Restart Apache Server
Restart Apache Server to apply changes
$ sudo service apache2 restart
That’s it. Now your website will enforce HTTP Strict Protocol Security policy on web browsers. You can use an online tool like Qualsys SSL Labs to check if HSTS is working properly on your website.
Also read : How to Change Apache Log Location
Related posts:
How to Change Default Page in .htaccess
How to Implement SSL/TLS in Apache Tomcat
How to Change XAMPP Apache Server Port
Apache Http Server vs Apache Tomcat Server
How to Disable Configuration File in Apache
How to Filter Logs Between Date Range in Linux
How to Redirect POST Request Data in .htaccess
.htaccess Make Subfolder Root

Sreeram has more than 10 years of experience in web development, Python, Linux, SQL and database programming.