Public Keys are required to get access to remote servers such as SSH server, or service such as GitHub. Many times new developers run tools like ssh-keygen or PuTTYgen to generate public-private key pairs. But they don’t know where it is located. So they are unable to submit their public keys to remote services such as GitHub or even local applications like PuTTY. In this short article, we will learn how to get your public SSH key files.
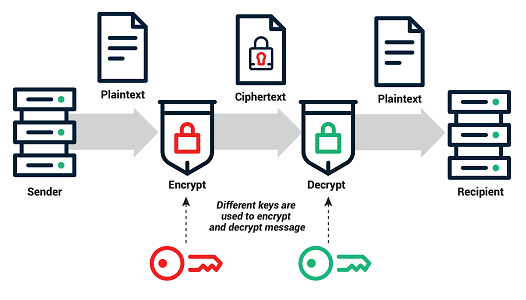
A public key is generally a large alphanumeric string used to encode data, generated by software or provided by trusted third-party authorities. Every public key matches to only one private key. Together, they are used to encrypt and decrypt messages. If you encode a message using a person’s public key, they can only decode it using their matching private key. These keys are used for user authentication whereby your user credentials are encrypted/decrypted using these public-private key pairs.
How to Get My Public SSH Key
We have assumed that you have indeed generated a key-pair on your system. By default, public key pairs are not present in Linux or Windows system. They need to be explicitly generated using third party tool like OpenSSH (ssh-keygen) or PuTTYgen.
On Linux & Mac systems, you will find your public key located at ~/.ssh. These keys have extension of .pub. So you can easily list all public keys in your system with the following command.
$ ls ~/.ssh/*.pub
On Windows, they are located at C:/Users/<your username>/.ssh folder.
These are the default locations where public keys are stored, unless you specifically generated them at another location.
In this short article, we have learnt how to find the location of public keys in Linux, Mac & Windows systems. It is important to keep track of your public keys and protect your private keys from exposure.
Also read:
How to Revoke SSH Access & Keys in Linux
How to Create Man Pages for Script, Package & Library
How to Keep SSH Session Alive After Disconnect
How to Limit CPU Usage Per User
How to Automate MySQL_Secure_Installation