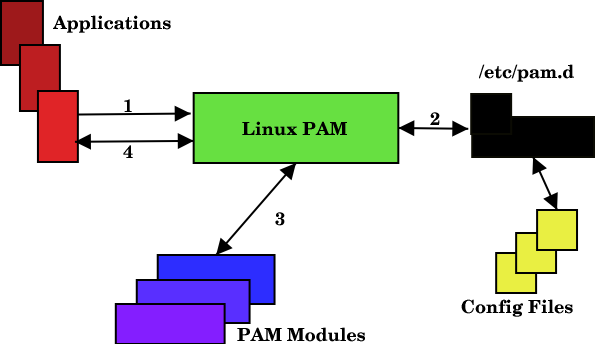
PAM (Pluggable Authentication Modules) is a powerful suite of libraries that allows you to implement dynamic user authentication in an application or process in Linux. It provides a high-level API that you can easily use in your applications, scripts & processes for user authentication. It allows developers to code their applications & scripts without worrying about user authentication, which is handled by PAM. In this article, we will look at how to configure PAM for your Linux system. It is available in almost every Linux distribution.
How to Configure PAM in Linux
Here are the steps to configure PAM in Linux. As a system administrator, you only need to be familiar with how PAM connects to your applications.
1. Check if application in PAM compatible
First, we need to check if a given application is compatible with PAM. You can easily do this using ldd command and checking if it was compiled with PAM library. Here is an example to check if SSH server is PAM compatible.
$ sudo ldd /usr/sbin/sshd | grep libpam.so
2. Configure PAM in Linux
/etc/pam.d folder contains application-specific configuration rules for PAM while its main configuration file is located at /etc/pam.conf. If there are application-specific files in /etc/pam.d then PAM will ignore its main /etc/pam.conf file.
The main configuration consists of rules of the following format
service type control-flag module module-arguments
- service: application/process/script name.
- type: module type/context/interface.
- control-flag: indicates action to be taken in case of authentication failure
- module: absolute filename or relative pathname of PAM.
- module-arguments: space separated list of arguments for controlling module behavior
The configuration rules in files in /etc/pam.d folder have the following syntax
type control-flag module module-arguments
Since the above rule is already present in application-specific file, you don’t need to mention the service name in /etc/pam.d folder.
Here is an example in /etc/pam.d/sshd file that prevents non-root login
account required pam_nologin.so
In the above syntax, the module field can take the following values.
- account: provide services for account verification and authentication
- authentication: user authentication
- password: for password management and user authentication
- session: applicable at the beginning of a session and end of a session
control-flag field above can take the following values
- requisite: in case of success proceed further. in case of failure record and report it to application, and stop checking further.
- required: in case of success proceed further. in case of failure record and report it to application, and continue checking further.
- sufficient: if all preceding modules have succeeded, the success of this module leads will return control to application. in case of failure, continue checking
- optional: success/failure is option for this module
- include/substack: include all lines of another config file
In this article, we have learnt how to configure PAM for user authentication in applications/scripts/tasks/processes in Linux. It is quite complicated but allows you to configure for which modules you want Linux to check for authentication and what actions to be taken in case of success/failure. It eliminates the need to build your own authentication system for every application. PAM offers an authentication API that you can plug into different modules of your application.
Also read:
How to Read Large CSV File in Python
How to Get Filename from Path in Python
How to Increase SSH Connection Timeout
How to Run Sudo Command Without Password
How to Save Dictionary to File in Python